MoveIT Data Breach



Realign the Start Button
The first thing that will jump out at you is the placement of the Start button. Long located in the lower-left corner of the screen, it’s now centered with the rest of the icons on the taskbar. But don’t worry, you can change it back.
Right-click the taskbar and open Taskbar Settings. Select the Taskbar Behaviors drop-down and change Taskbar Alignment to Left.
Your taskbar icons move to the left and the Start button goes back where it belongs. For more on personalizing the Windows 11 taskbar, check out our guide.
Add More Options to Your Right-Click Menu
The right-click menu now focuses only on the most important settings. Should you need more settings—print, set a new background, or view the full file location, for instance—select Show more options to open a spill-over menu.
Customize the Quick Settings Panel
Windows 11 separates the Quick Settings that appear in the Action Center in Windows 10 from that panel’s notifications. Click the area of the taskbar that has Wi-Fi, speaker, and, battery icons to open a settings menu that lets you control Wi-Fi, Bluetooth, airplane mode, battery-saver mode, and more. To add or remove settings buttons, click the pencil-shaped Edit quick settings button. Unpin what you don’t want or click Add to make new features accessible from the Quick Settings menu.
Add Tabs to File Explorer
A top feature added in the Windows 11 22H2 update is that File Explorer finally gets tabs like its macOS counterpart Finder has had for years. Having tabs saves you from littering your desktop with multiple File Explorer windows when you need to view more than one at a time. Just right-click on a folder and choose Open in New Tab, like you would in a web browser.
Pro tip: You can drag a file between tabs. Just drag it to the desired tab and then down into the file list for that tab. Also as with a web browser, you can drag tabs sideways to rearrange them and hit Alt-Left Arrow to navigate back in a tab.
With the initial Windows 11 release, Microsoft streamlined the ribbon at the top of the File Explorer menu. Cut, Copy, Paste, Rename, Share, Delete, Sort, and View choices get prominent buttons at the top, saving you from having to wade through multiple menus you seldom use. Windows 11 also adds a New button for creating new folders and shortcuts, as well as documents based on the programs you have installed. The buttons displayed change based on context, too, so, for example, when you’re searching in the right-hand search box, you get a Search Options button.

Google announced today that the Google Chrome web browser will likely drop support for Windows 7 and 8.1 starting February 2023.
After support is discontinued for these two Windows versions, the company says Chrome users must ensure that their devices are running at least Windows 10.
“With the release of Chrome 110 (tentatively scheduled for February 7th, 2023), we’ll officially end support for Windows 7 and Windows 8.1,” Google Chrome Support Manager revealed.
“You’ll need to ensure your device is running Windows 10 or later to continue receiving future Chrome releases.”
Google’s decision to drop support for these platforms matches Microsoft’s Windows lifecycle policy, which lists the Extended Security Update (ESU) program for Windows 7 and the Windows 8.1 end of support on January 10, 2023.
Currently, Windows 7 is still running on over 10% of all Windows systems worldwide, while Windows 8.1 is just 2.7%, according to Statcounter GlobalStats.
The Google Chrome web browser has a market share of over 65%, followed by Safari with roughly 18% and Microsoft Edge with 4.32% (which uses the Chrome rendering engine with enhancements from Microsoft).
Even though older Google Chrome versions will work even after support is dropped on Windows 7 / 8.1, Google advises users to upgrade their systems to keep receiving security updates.
This matches Microsoft’s advice for customers with systems running Windows versions out of support which no longer receive technical assistance or software updates, exposing their computers and data to security risks.
“Older versions of Chrome will continue to work, but there will be no further updates released for users on these operating systems,” the Google employee added.
“If you are currently on Windows 7 or Windows 8.1, we encourage you to move to a supported Windows version before that date to ensure you continue to receive the latest security updates and Chrome features.”
Follow us on Facebook for more news and Tips
Enhance Computer LLC

From PCMag.com
https://www.pcmag.com/how-to/how-to-avoid-social-media-scams
As long as social media platforms have been around, there have been hackers attempting to take control of accounts. Remember MySpace? My friends’ page for their band was hacked a number of times, sometimes by malicious strangers, sometimes by overzealous fans. Back then, if a hacker got into your MySpace account, they had access to your friends’ list, private messages, photos, and blog posts. It was a lot, but it’s nothing like the treasure trove of information many of today’s social media accounts contain.
Facebook accounts often contain your real name, email address, birth date, relationship status, and physical address. In addition to storing all your private messages, photos, and feed posts, Facebook is also used to log in to other websites. If a hacker manages to take over your Facebook account, they may have access to some of your other accounts around the web. The same goes for Instagram, which is also owned by Meta.
Criminals need all your personally identifiable information (PII) to commit identity fraud or to sell your account to the highest bidder. According to a report from Privacy Affairs(Opens in a new window), the cost of a Facebook account on the dark web is $45. An Instagram account goes for $40.
According to the Identity Theft Resource Center(Opens in a new window) (ITRC), the internet safety organization received nearly 500 social media account takeover reports in the first three months of 2022. That’s up from the 320 the ITRC received in 2021. Experts at the organization say criminals are committing Instagram scams by posing as a “friend” of the victim. The hacker lures in their victim with an email or a private message stating they need help getting back into their Facebook or Instagram account. The hacker sends a malicious link in their message, and when the victim clicks on it they lock themselves out of their account and give access to the hacker.
The demand for hacked social media accounts is high. Don’t let yourself be caught off guard by a scammer. Take the following steps to keep your account locked down and secure.
If you believe your Instagram account has been hacked, here are six steps to take.
From PCMag.com
Taking a screenshot on your Android device sounds like a simple task. You just hit a few buttons and the screen is saved to your phone. However, Android devices are not as uniform as iPhone, so methods can differ depending on the device manufacturer and OS version you’re running.
Phones from Samsung, Google, Motorola, and OnePlus all have built-in screenshot capabilities. And if you’re running the most recent version of the Android operating system, you get even more features. Here’s how to take a screenshot on your Android phone.

Google Pixel 4a 5G (Credit: Steven Winkelman)
Most recent Android devices have standardized the screenshot action to pressing the Power and Volume Down buttons simultaneously. Others may have you press down on the Power button, then select Screenshot from the menu.
On a Pixel phone, you can swipe up from the bottom of the screen to open your recent apps, then tap Screenshot to capture the current app. Older phones with a physical home button on the front may require you to press the Power and Home buttons together.
If your phone has Google Assistant, you can use a voice command to ask it to take a screenshot for you. Say something like “OK Google, take a screenshot” and the action is completed.

Samsung Galaxy S22 Ultra with S Pen (Credit: Molly Flores)
For Samsung Galaxy devices using the S Pen stylus, you can hold down the button on the S Pen and scribble across the screen to take a screengrab. Another way is to remove the pen from the phone and tap Smart Select from the menu. You can then choose between a square, free, or circle capture area, then draw to capture the screen.
There will be a “flash” on the screen and the sound of a shutter (if you have the sound on), then the shot should show up in your photo library.
From PCMag
Scammers have been exploiting deepfake technology to impersonate job candidates during interviews for remote positions, according to the FBI.
The agency has recently seen an increase in the number of complaints about the scam, the FBI said in a public advisory(Opens in a new window) on Tuesday. Fraudsters have been using both deepfakes and personal identifying information stolen from victims to dupe employers into hiring them for remote jobs.
Deepfakes involve using AI-powered programs to create realistic but phony media of a person. In the video realm, the technology can be used to swap in a celebrity’s face onto someone else’s body. On the audio front, the programs can clone a person’s voice, which can then be manipulated to say whatever you’d like.
The technology is already being used in YouTube videos to entertaining effect(Opens in a new window). However, the FBI’s advisory shows deepfakes are also fueling identity theft schemes. “Complaints report the use of voice spoofing, or potentially voice deepfakes, during online interviews of the potential applicants,” the FBI says.
The scammers have been using the technology to apply for remote or work-from-home jobs from IT companies. The FBI didn’t clearly state what the scammers’ end goal. But the agency noted, “some reported positions include access to customer PII (personal identifying information), financial data, corporate IT databases and/or proprietary information.”

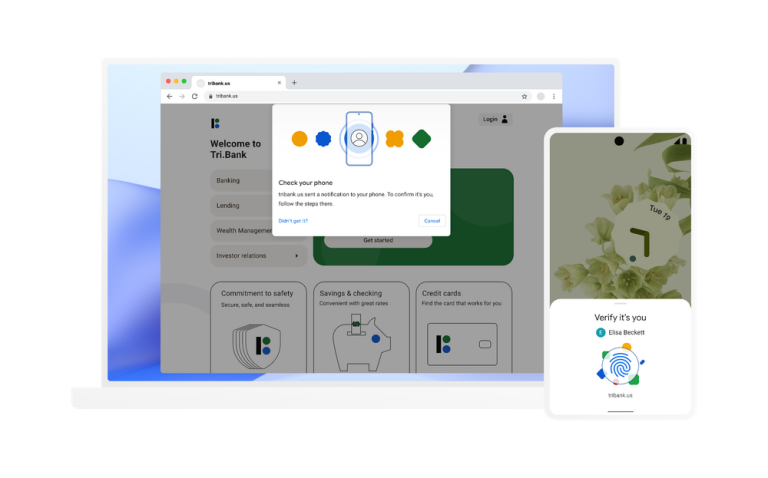
The IT industry is taking another big step toward embracing password-less technology. Three major companies—Apple, Google, and Microsoft—are adopting a new login system that ditches passwords and relies on your smartphone or laptop to authenticate your sign-ins.
“This will simplify sign-ins across devices, websites, and applications no matter the platform — without the need for a single password,” Google said in the announcement. “These capabilities will be available over the course of the coming year.”
Google has been among the vendors pushing the tech industry to drop passwords for simpler, more secure ways to grant login access. To do so, the company has been using the smartphone as a way to authenticate a user’s login. Rather than type in a password, you can simply go to your phone and unlock access to the internet account on your PC. From there, the Android phone can sign an authentication request via Bluetooth to the PC, logging you in.
The problem is that current password-less approaches don’t always work from one hardware platform to another. Functionality can also be lost if you’re signing in from a new device.
To fix this, Apple, Google, and Microsoft plan on adopting an upgraded password-less login method called “multi-device FIDO credential,” which is designed to work across platforms.
The system comes from the FIDO Alliance, a consortium of companies that have been working on standards and protocols around dropping passwords. “Until now, users were required to enroll their FIDO credentials for each service on each new device, typically with a password for that first sign-in. With multi-device FIDO credentials, the credentials are available to users whenever they need them—even if they replace their device,” the Alliance said.
Credit PC Magazine for the Story

While not as common as they used to be, adware programs bombard their victims with advertisements. Sometimes they’re ads for legitimate products, netting an affiliate fee for the adware perpetrator any time someone clicks on the ad. Other times they contain links to malicious websites that will attempt to drop more malware on your PC.
Not every site redirect is malicious, but if you find that trying to reach DuckDuckGo or Google takes you to an unfamiliar search site, you’ve got a problem. Sometimes the redirection is less noticeable. For example, a banking Trojan might divert your browser to a fraudulent site that looks just like your bank’s real site. In that case your only clue is the unfamiliar URL in the Address bar. Redirection attacks often rely on browser extensions, so if you suspect a problem, dig into your browser settings and disable or delete any extensions that you didn’t install deliberately. While you’re there, disable any extensions that you don’t use on a regular basis.
Creating and distributing fake antivirus programs (also called scareware) is a lucrative business. The perpetrators use drive-by downloads or other sneaky techniques to get the fake antivirus onto your system, then display alarming warnings about made-up security threats. Scanning for malware with the fake AV is free and super-fast since it’s not actually doing anything. But if you naively ask the fake AV to fix the problems it found, you’ll find it demands cash on the barrelhead first.
Malware focused on Facebook and other social media sites propagates by generating fake posts or DMs. Typically, these posts include an inflammatory statement of some kind, like “OMG were you really that drunk? Look at this picture!” Anyone who falls for the fake and clicks the link becomes the malware’s next victim.
Some malware programs literally hold your PC or data for ransom. Overt ransomware threats encrypt all your pictures and documents and demand that you pay to get them back. Even worse are the ones that encrypt your entire computer, rendering it useless unless you pay to have it unlocked. Others are all bluff and bluster. For example, they may display a warning, purportedly from the FBI or another agency, stating that your computer was used to send spam or view porn, and demanding that you pay a fine before you’re allowed to use it again. Of course, even if you do pay, you may not get your documents back. Antivirus apps and security suites should protect against most malware, but you can also double down on safety by adding a dedicated ransomware protection software to your security arsenal.
A smart user, suspecting the presence of malware, might launch Task Manager to investigate, or check settings using Registry Editor. If you suddenly find that trying to use these or other system tools triggers a message saying your Administrator has disabled them, it may well be an attempt at self-defense by malware on your system.
That’s right. Some types of malware do their best to hide all activity, leaving no visible traces. Even when you don’t notice anything unusual, it’s possible that a bot on your system may be quietly awaiting instruction from its command and control system, perhaps to participate in a DDoS (Distributed Denial of Service) attack. A Remote Access Trojan (or some other form of spyware) may be harvesting your personal information, keeping quiet so you don’t notice.
If you think that malware has taken up residence in your PC, install a powerful antivirus application or security suite immediately. Already got one? Then apparently the malware got past its protection—it happens. Manually run an update to make sure your antivirus has the latest malware definitions and then run a full scan.
If you still have an unwanted app your regular security software can’t get rid of (or you just want to be doubly sure your system is clean) you can scan your PC again with an aggressive cleanup-only tool such as Malwarebytes. Do whatever it takes to get that nasty, malicious program out of your system as soon as possible, before it invites friends to make your security problems even worse.
Credit PC Mag for This Article